CLOUD DESTINATIONS SECURITY
Cybersecurity challenges demand an organization to face two facts.
First, the protection of critical company and customer
information which is a
business requirement to protect the company's reputation and enterprise value.
Second, even the best programs will experience failure
and expose some information
the company would like to protect.
At Cloud Destinations, we believe confidence in security and privacy does not come from knowing nothing will happen, it is achieved by knowing all the things that can happen and preparing both proactive and reactive solutions.
Holistic approach starts by understanding what is most important to you, also as applicable to your business such as PCI DSS, SOC 1, HIPAA, then structuring and supporting the program so that your business is engineered to grow securely.
- Identity & Access Management
- Vulnerability Assessment & Penetration Testing
- Infrastructure Security
- Endpoint Security
- Security Operations Center
- GRC Implementation

Values We Live By
Honesty
First and foremost, we need to be honest with you and all of your stakeholders. We don't always have good news to deliver in auditing and consulting, but the best service we can render to you is to be honest and straightforward regarding our findings and opinions. We value your trust and strive each day to continue to maintain it.
Transparency
It is our goal to be absolutely transparent regarding the scope of our services, what is included or excluded, and the pricing for what we undertake to perform. All parties benefit from clear and concise agreements, and we try our utmost to deliver what we commit to, when we commit to it without surprise charges, other 'fees', or similar gimmicks.
Expertise
Professional expertise to undertake a given project is critical in our industry. If we don't have the expertise to take on a given project, we'll be up-front with you and try to guide your resources that fit your needs. We do undertake an engagement, our reputation is on the line that we can complete it in a competent and professional manner.
Our Services
Cloud destinations offers variety of services that help secure your business.
To know more select the service you are interested in.
Vulnerability Assessment & Penetration Testing
VA & PT is considered the most efficient way to identify where your organization's weaknesses are and what are
the key risk areas that need to be addressed.
At Cloud Destinations we help your organization discover your assets, detect and mitigate potential
vulnerabilities exploitable by hackers. Thereby reducing the threat landscape and keeping the attack surface
as small as possible.
Cloud Destinations helps in setting up a routine vulnerability assessment as per your needs for various
compliance programs such as PCI, HIPAA and ISO 27001.
Our services include the following :
- Internal / External Network Vulnerability Scans
- Web Application Assessment
- Secure Code Review (SAST / DAST)
- External Penetration Testing (Black Box, White Box, Grey Box)
Read full description of services
Identity and access management (IAM)
We at Cloud Destinations help you implement IAM to establish a strong Identity, Authentication, Authorization and Accountability (IAAA) for your business. Based on the organization's needs we provide services as following but not limited to:
- Active Directory
- User Management
- Single-Sign-On
- Multi Factor Authentication
- Password Policy
- Role Based / Privileged Access Management
Read full description of services
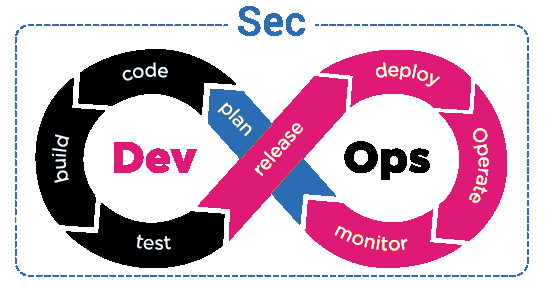
DevSecOps
DevSecOps is the natural extension of DevOps. The process is meant to do two things: It can either take the benefits that DevOps gives to the development and operations branches of your IT department and extend them to the security team or it can integrate the security processes that need to be done into the DevOps team. In Cloud Destinations, we provide the following services in DevSecOps.
- Cloud Security Assessment
- Automation & Configuration Management
- Security tooling & Software Delivery Pipeline in CI/CD
Read full description of services
Infrastructure Security
Infrastructure is considered the root of your corporate security plan. Cyber attacks on critical
infrastructure have become increasingly complex and disruptive, causing systems to shut-down,
halting operations, or simply enabling attackers to remotely control affected servers.
Cloud Destination offers a wide range of security at the perimeter level with a layered
approach such as Defense-in-depth, Zero Trust.
Services offered include but are not limited to:
- Security Baselining with frameworks such as CIS Top 20
- Patch Management
- Network Security (IDS, IPS, Firewall, VPN)
- Disaster Recovery
Read full description of services
Endpoint Security
- Data loss prevention
- Insider threat protection
- Disk, endpoint, and email encryption
- Application whitelisting or control
- Network access control
- Data classification
- Endpoint detection and response
- Privileged user control
- Anti-virus and anti-malware
Read full description of services
Security Operations Center
Having a centralized location in dealing with security issues at an organization
and technical level is what Cloud Destinations aims in developing with its SOC implementation.
We incorporate various frameworks such as the MITRE ATT&CK, Cyber Kill Chain alongside a
robust Incident response framework to proactively detect, contain, respond and prevent attacks.
We help our customers in implementing:
- Implement and Manage SIEM
- Indicators of Compromise
- Incident Management
- Threat Management
Read full description of services
GRC Implementation
Cloud Destination helps organizations focus on achieving their objectives and goals by taking the necessary measures
to keep their business aligned with Information Security standards. In order to accomplish that,
it is ideal to adopt required regulatory requirements of various geographies.
Our consultants are certified experts across several domains such as CISA, CISSP.
- Implement Risk Management
- Security Frameworks (NIST CSF, ISMS)
- Business Continuity
- IS Audit (Internal / External)
- Security Compliance Readiness ( ISO 27001, PCI DSS , HIPAA, QECP)
Read full description of services




 Follow us on linkedin
Follow us on linkedin